As hinted in Phish with no smell , some scams are hard to detect. How hard?
False confidence
Let’s try 7 Ways to Recognize a Phishing Email (published on Security Metrics).
| Assertion | Real world |
|---|---|
| Legit companies don’t request your sensitive information via email | Actually, they do. Many accountants and lawyers ask for sensitive documents be sent to them by email. |
| Legit companies usually call you by your name | So do scammers. I regularly receive spam containing my name |
| Legit companies have domain emails | So do scammers. See the Salvation Army example above. |
| Legit companies know how to spell | So do scammers. See the Salvation Army example. |
| Legit companies don’t force you to their website | Actually, they do. Paypal, banks and airlines require you to visit their website to get even routine information. Software vendors commonly send whitepapers as individualised links to their website. Training organisations commonly send tokenised links to webinars or videoconferenced meetings that nonetheless require sign-in through a portal. |
| Legit companies don’t send unsolicited attachments | Actually, they do. Many include a banner or footer which are detected by email readers as attachments or embedded images. Outsourced services, such as our voicemail system, may deliver unexpected attachments. |
| Legit company links match legitimate URLs | So do scammers. Some scammers use realistic substitute URLS (as in the Salvation Army example above) and some use real links, to cheaply add authenticity. |
The danger with the rules above is that they are such strong assertions.
A better guide
Take precautions. (See Scamwatch)
- Do not click links or attachments (or add apps or extensions) that you did not expect.
- Google the wording of a message to find out whether others have reported it.
- Expect a secure (https) site – a closed padlock on the address bar.
- Never provide personal details to a caller. Call the organisation through its official channels yourself.





 While we do try to make their work as fluid as possible, executives need to understand:
While we do try to make their work as fluid as possible, executives need to understand: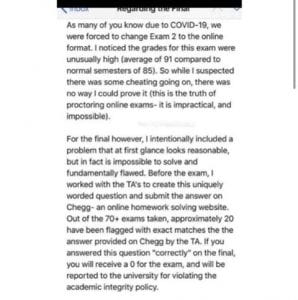 Lecturer statement reported by students:
Lecturer statement reported by students: